Traffic, Organic Evergreen Traffic is a lot of work and it takes skill and timing and it has many complex pieces to the wound up Watch machine that it truly is!
Internet traffic is the flow of data across the Internet.
Because of the distributed nature of the Internet, there is no single point of measurement for total Internet traffic.
Internet traffic data from public peering points can give an indication of Internet volume and growth, but these figures exclude traffic that remains within a single service provider's network as well as traffic that crosses private peering points.
The phrase "Internet traffic" is sometimes used to describe web traffic, the amount of data sent and received by visitors of a particular web site.
Traffic sources
File sharing constitutes a large fraction of Internet traffic.[1]The prevalent technology for file sharing is the BitTorrent protocol, which is a peer-to-peer (P2P) system mediated through indexing sites that provide resource directories.
The traffic patterns of P2P systems are often described as problematic and causing congestion.[2]
According to a Sandvine Research in 2013, Bit Torrent’s share of Internet traffic decreased by 20% to 7.4% overall, reduced from 31% in 2008.[3]
Streaming media provides users with video and audio resources, such as YouTube and Spotify.
Traffic management
The Internet does not employ any formally centralized facilities for traffic management.
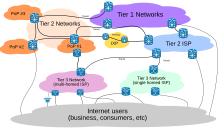
Its progenitor networks, especially the ARPANET established early backbone infrastructure which carried traffic between major interchange centers for traffic, resulting in a tiered, hierarchical system of internet service providers (ISPs) within which the tier 1 networks provided traffic exchange through settlement-free peering and routing of traffic to lower-level tiers of ISPs.
The dynamic growth of the worldwide network resulted in ever-increasing interconnections at all peering levels of the Internet, so that a robust system developed that could mediate link failures, bottlenecks, and other congestion at many levels.[citation needed]
Tax on Internet use
A planned tax on Internet use in Hungary introduced a 150 forint (US$0.62, €0.47) tax per gigabyte of data traffic, in a move intended to reduce Internet traffic and also assist companies to offset corporate income tax against the new levy.[4]Hungary achieved 1.15 billion gigabytes last year and another 18 million gigabytes accumulated by mobile devices. This would have resulted in extra revenue of 175 billion forints under the new tax based on the consultancy firm eNet.[4]
According to Yahoo News, economy minister Mihály Varga defended the move saying "the tax was fair as it reflected a shift by consumers to the Internet away from phone lines" and that "150 forints on each transferred gigabyte of data – was needed to plug holes in the 2015 budget of one of the EU’s most indebted nations".[5]
Some people argue that the new plan on Internet tax would prove disadvantageous to the country’s economic development, limit access to information and hinder the freedom of expression.[6]
Approximately 36,000 people have signed up to take part in an event on Facebook to be held outside the Economy Ministry to protest against the possible tax.[5]
Traffic classification
Traffic classification describes the methods of classifying traffic by observing features passively in the traffic, and in line to particular classification goals. There might be some that only have a vulgar classification goal.For example, whether it is bulk transfer, peer to peer file sharing or transaction-orientated. Some others will set a finer-gained classification goal, for instance the exact number of application represented by the traffic.
Traffic features included port number, application payload, temporal, packet size and the characteristic of the traffic.
There are a vast range of methods to allocate Internet traffic including exact traffic, for instance port (computer networking) number, payload, heuristic or statistical machine learning.[7] are the main methods.
Accurate network traffic classification is elementary to quite a few Internet activities, from security monitoring to accounting and from quality of service to providing operators with useful forecasts for long-term provisioning.
Yet, classification schemes are extremely complex to operate accurately due to the shortage of available knowledge to the network.
For example, the packet header related information is always insufficient to allow for an precise methodology. Consequently, the accuracy of any traditional method are between 50%-70%.
Bayesian analysis techniques
Work[8] involving supervised machine learning to classify network traffic.Data are hand-classified (based upon flow content) to one of a number of categories.
A combination of data set (hand-assigned) category and descripttions of the classified flows (such as flow length, port numbers, time between consecutive flows) are used to train the classifier.
To give a better insight of the technique itself, initial assumptions are made as well as applying two other techniques in reality.
One is to improve the quality and separation of the input of information leading to an increase in accuracy of the Naive Bayes classifier technique.
The basis of categorizing work is to classify the type of Internet traffic; this is done by putting common groups of applications into different categories, e.g., "normal" versus "malicious", or more complex definitions, e.g., the identification of specific applications or specific Transmission Control Protocol (TCP) implementations.[9]
Adapted from Logg et al.[10]
Survey
Traffic classification is a major component of automated intrusion detection systems.[11][12][13]They are used to identify patterns as well as indication of network resources for priority customers, or identify customer use of network resourrs that in some way contravenes the operator’s terms of service.
Generally deployed Internet Protocol (IP) traffic classification techniques are based approximately on direct inspection of each packet’s contents at some point on the network.
Source address: port and destination address are included in successive IP packet's with similar if not the same 5-tuple of protocol type. ort are considered to belong to a flow whose controlling application we wish to determine.
Simple classficaiton infers the controlling application’s identity by assuming that most applications consistently use’ well known’ TCP or UDP port numbers.
Even though, many candidates are increasingly using unpredictable port numbers. As a result, more sophisticated classification techniques infer application type by looking for application-specific data within the TCP or User Datagram Protocol (UDP) payloads.[14]
Global Internet traffic
Aggregating from multiple sources and applying usage and bitrate assumptions, Cisco Systems, a major network systems company, has published the following historical Internet Protocol (IP) and Internet traffic figures:[15]Year |
IP Traffic (PB/month) |
Fixed Internet traffic (PB/month) |
Mobile Internet traffic (PB/month) |
|---|---|---|---|
| 1990 | 0.001 | 0.001 | n/a |
| 1991 | 0.002 | 0.002 | n/a |
| 1992 | 0.005 | 0.004 | n/a |
| 1993 | 0.01 | 0.01 | n/a |
| 1994 | 0.02 | 0.02 | n/a |
| 1995 | 0.18 | 0.17 | n/a |
| 1996 | 1.9 | 1.8 | n/a |
| 1997 | 5.4 | 5.0 | n/a |
| 1998 | 12 | 11 | n/a |
| 1999 | 28 | 26 | n/a |
| 2000 | 84 | 75 | n/a |
| 2001 | 197 | 175 | n/a |
| 2002 | 405 | 356 | n/a |
| 2003 | 784 | 681 | n/a |
| 2004 | 1,477 | 1,267 | n/a |
| 2005 | 2,426 | 2,055 | 0.9 |
| 2006 | 3,992 | 3,339 | 4 |
| 2007 | 6,430 | 5,219 | 15 |
| 2008 | 9,927 | 7,639 | 38 |
| 2009 | 14,414 | 10,676 | 92 |
| 2010 | 20,197 | 14,929 | 256 |
| 2011 | 27,483 | 20,634 | 597 |
| 2012 | - | 31,338 | 885 |
"Fixed Internet traffic" refers perhaps to traffic from residential and commercial subscribers to ISPs, cable companies, and other service providers.
"Mobile Internet traffic" refers perhaps to backhaul traffic from cellphone towers and providers.
The overall "Internet traffic" figures, which can be 30% higher than the sum of the other two, perhaps factors in traffic in the core of the national backbone, whereas the other figures seem to be derived principally from the network periphery.
Internet backbone traffic in the United States
The following data for the Internet backbone in the US comes from the Minnesota Internet Traffic Studies (MINTS):[16]| Year | Data (TB/month) |
|---|---|
| 1990 | 1 |
| 1991 | 2 |
| 1992 | 4 |
| 1993 | 8 |
| 1994 | 16 |
| 1995 | n/a |
| 1996 | 1,500 |
| 1997 | 2,500–4,000 |
| 1998 | 5,000–8,000 |
| 1999 | 10,000–16,000 |
| 2000 | 20,000–35,000 |
| 2001 | 40,000–70,000 |
| 2002 | 80,000–140,000 |
| 2003 | n/a |
| 2004 | n/a |
| 2005 | n/a |
| 2006 | 450,000–800,000 |
| 2007 | 750,000–1,250,000 |
| 2008 | 1,200,000–1,800,000 |
| 2009 | 1,900,000–2,400,000 |
| 2010 | 2,600,000–3,100,000 |
| 2011 | 3,400,000–4,100,000 |
The Cisco data can be seven times higher than the Minnesota Internet Traffic Studies (MINTS) data not only because the Cisco figures are estimates for the global—not just the domestic US—Internet, but also because Cisco counts "general IP traffic (thus including closed networks that are not truly part of the Internet, but use IP, the Internet Protocol, such as the IPTV services of various telecom firms)".[17]
The MINTS estimate of US national backbone traffic for 2004, which may be interpolated as 200 petabytes/month, is a plausible tree-fold multiple of the traffic of the US's largest backbone carrier, Level(3) Inc., which claims an average traffic level of 60 petabytes/month.[18]
Source: Wikipedia.org, Creative Commons Attribution-Share Alike 3.0 Unported
P. S. There is a better, quicker, and easier way to get Traffic! High Quality North American Traffic! Pay for it!
Yea I know You don't have the money right? No Traffic equals no money and no possibility of any chance of receiving money or the opportunities to earn money! Remember Time is Money!
Somebody Come and Play Today! Earn as You Learn, Grow as You Go!
The Man Inside the Man
from
Sinbad the Sailor Man
A
JMK's Production
Share this page, If you liked It Pass it on, If you loved It Follow Me!
TTFN
CYA Later Taters!
Thanks for stopping by.
Donnie/ Sinbad the Sailor Man
P.S. Do You Want To Make Money Like Google And Facebook?


No comments:
Post a Comment